1
2012
What is Database Security?
Database security is a series of processes and systems which are put in place to protect the database from any outside source that has a malicious intent or from anyone inadvertently accessing the database, whether they may be authorized or not. There are other security measures in place such as firewalls and routers, and these are some examples of those handling the external security of the database. Likewise, there are also network security systems in place to detect any malicious activity within the network. There […]
3
2012
What is a Transactional Database?
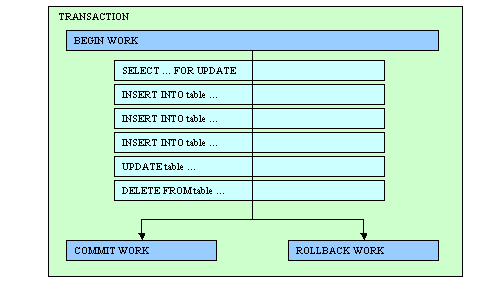
Whenever a user stores or manages data in the database, the user is making a “database transaction”. The database transaction refers to the work done within a database management system or less likely against a database. The transaction in the database works independently with other transactions, so users can ensure that all data are coherent, accessible and secure. The significance of making transactions with a database is to provide a more cohesive and coherent transferring of data as well as keeping the data secure from […]
21
2012
What is Database Auditing?
Database auditing is the method done by database administrators in order to see the actions of its users. This procedure is often done to make sure that the database is accessed only by those who are allowed. The security of the database is, of course, the main priority of the administrator, thus, the need of database auditing. Database auditing can be based on a single or a combination of actions. Security measures will be activated once you, as the administrator, emphasize the keys that will […]
16
2012
What is Database Encryption?
Nowadays, information is one of the most valuable commodities. The internet has enabled people to share information across the globe. Unfortunately, there are people who have found ways to take advantage of this as cyber crimes are now as common as the ones done in the streets. Like the criminals in the real world, thieves in the internet also adapt to the changes in their playing field, and these criminals gain or use their knowledge to take advantage of unsuspecting victims. Due to this, IT […]
Advertisements
Recent Posts
- What is a Disaster Recovery Data Center
- What is a Relational Database?
- What is a Flat File Database?
- What is a DSN or Database Source Name?
- What is a Disaster Recovery Plan?
- What is an Open Source Database?
- What is Disaster Recovery?
- What is a Database Cluster?
- What are Database Servers?
- What are Database Forms?
Random Posts
- What are High Availability Servers?
- What is a Relational Database?
- What is a Flat File Database?
- What is a Stored Procedure?
- What is Data Integration?
- Create your first Mysql database
- What is a DSN or Database Source Name?
- What is a Disaster Recovery Data Center
- What is Enterprise Information Integration
- What is Database Hosting?


 An article by
An article by